Unauthorized creation or tampering of resourses by unauthenticated user
This finding is used to indicate that an API commonly used to tamper with resources in a Kubernetes cluster was invoked by an unauthenticated user.
To simulate this we'll create two role resources, pod-create and psp-use.
Once the role is created we'll need to bind it with the system:anonymous user. Below command will create rolebinding named pod-access and psp-access binding the roles pod-create and psp-use to the user named system:anonymous.
Note that the above rolebinding command will trigger Policy:Kubernetes/AnonymousAccessGranted finding in guard duty within few minutes.
Now let us create a Pod named nginx using a HTTP post call.
apiVersion: v1
kind: Pod
metadata:
name: nginx
namespace: default
spec:
containers:
- name: nginx
image: nginx
ports:
- containerPort: 80
'
Verify if the Pod is Running.
NAME READY STATUS RESTARTS AGE
nginx 1/1 Running 0 2m17s
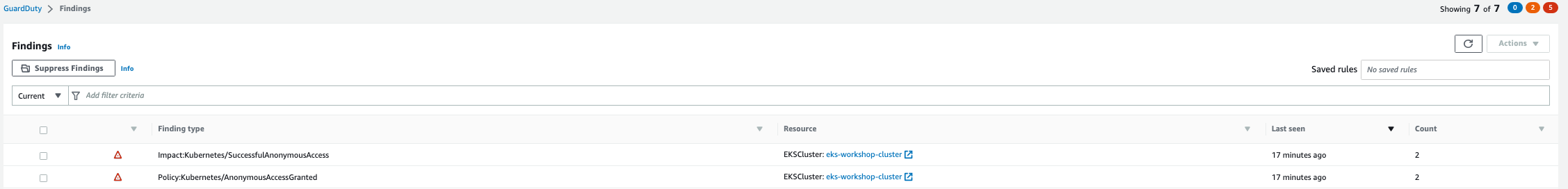
Within a few minutes we'll see the finding Impact:Kubernetes/SuccessfulAnonymousAccess in the GuardDuty portal.
Cleanup: